Ahmed Elmalla - Your Dedicated Computer Science Tutor | Learn with Kemo
Ahmed Elmalla - Your Dedicated Computer Science Tutor | Learn with Kemo Portfolio

Understanding Google Dorks: Advanced Search Techniques for Finding Website Vulnerabilities
Google Dorks: Leveraging Advanced Search for Website Security Vulnerabilities
Google Dorks is a powerful technique that utilizes specialized Google searches to uncover security vulnerabilities and sensitive information that is typically hidden or not easily accessible on a website. This technique is highly effective for identifying weaknesses in website security, making it a valuable tool for ethical hackers and cybersecurity professionals.
What is a Google Dork Query?
A Google Dork query, often simply called a "dork," is a custom search string that uses advanced search operators to retrieve specific information that wouldn’t normally be visible through standard search methods. This process, also known as Google hacking, can reveal details like exposed databases, unsecured files, login portals, and other sensitive data that could be exploited if left unprotected.
How Google Dorking Works:
By combining search operators with targeted keywords, Google Dorking enables users to filter through vast amounts of web data, isolating potentially vulnerable content. For example, queries can be constructed to find specific file types, directories, or even configuration files that may contain passwords or other critical information. This makes Google Dorks a go-to method for penetration testing and security assessments.
Ethical Use and Application:
While Google Dorking can be misused by malicious actors, it is also a critical technique for ethical hackers performing security audits. By identifying and addressing these vulnerabilities, organizations can better secure their online assets and protect sensitive information from unauthorized access.
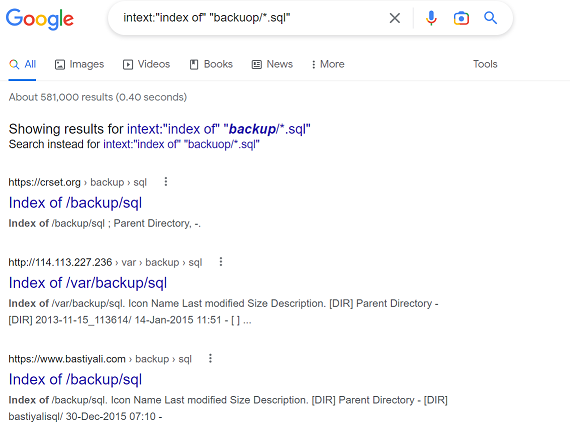
Google Dorking Query Examples: Identifying Vulnerable Data with Advanced Search Techniques
Google Dorking is a powerful tool for uncovering hidden or unsecured data on websites by using advanced search operators. Below are some examples of queries that can be used to find exposed files and directories:
Query Examples:
-
intitle:"Index of" *.xlsx
This query searches for directory indexes containing.xlsxfiles, potentially revealing exposed spreadsheets with sensitive data. -
intitle:final.attendee.list | inurl:final.attendee.list
This search finds files and URLs containing phrases like "final attendee list," which might lead to lists with names and contact details from events or conferences. -
intitle:"index of /" intext:".db"
This query locates directory indexes with.dbfiles, which could include unprotected databases containing critical information. -
"index of" :excel documents
This query targets directory indexes labeled as "index of" containing Excel documents, which could expose financial records, contact lists, or other private data.

Real-World Application and Lessons Learned:
Initially, our plan was to contact companies affected by these vulnerabilities to offer assistance in closing these security gaps. However, we quickly realized that these security holes are often overlooked by people with limited technical expertise. These are typically low-tech environments where critical security practices are either unknown or underutilized, leading to such exposures in the first place.